#cyberrisk #criticalinfrastructure #Apple
Critical Infrastructure to protect against Cyber Risk
A single point of failure (SPOF) is a part of an operation, that if it were to fail, could bring the entire operation to a halt or cause severe impact to other connected operations or society more broadly. SPOF exist in many operations and include hardware, software, mechanical infrastructure, assets, and key entities in supply chains. In most cases SPOF will impact the operation of the business itself such as the Southwest Airlines outage in 2016, where a single router failure caused the grounding of hundreds of the company’s flights over several days. Cyberattacks against critical infrastructure can take many forms including DDoS attacks, ransomware attacks, destructive malware attacks and unauthorized access to industrial control systems or hardware.
The increasing use of internet connected sensors, automated controls and remote access in critical infrastructure operations has inevitably led to a higher risk of cyberattacks aimed at these operations. However, the beginning of an alarming trend can be traced back to an attack that took place more than a decade ago. There were many historic critical infrastructure outages caused by natural catastrophe or system failure are at least somewhat useful in determining the consequences of cyberattacks on such infrastructure. Electricity is in itself very critical infrastructure, but all other critical infrastructure is also dependent on the power grid including water supply, energy supply, communication, transportation, healthcare, and banking. Finally, because cyberattacks are an entirely man-made threat, as opposed to the risks from natural hazards, motivation is an important factor in determining the probability of successful attacks.
Today's Headline in NewsHours
0:00 Intro
2:08 #CommerceIQ raises $60 million, looks to launch India operations by 2022
.

#cyberrisk #criticalinfrastructure #Apple
Critical Infrastructure to protect against Cyber Risk
A single point of failure (SPOF) is a part of an operation, that if it were to fail, could bring the entire operation to a halt or cause severe impact to other connected operations or society more broadly. SPOF exist in many operations and include hardware, software, mechanical infrastructure, assets, and key entities in supply chains. In most cases SPOF will impact the operation of the business itself such as the Southwest Airlines outage in 2016, where a single router failure caused the grounding of hundreds of the company’s flights over several days. Cyberattacks against critical infrastructure can take many forms including DDoS attacks, ransomware attacks, destructive malware attacks and unauthorized access to industrial control systems or hardware.
The increasing use of internet connected sensors, automated controls and remote access in critical infrastructure operations has inevitably led to a higher risk of cyberattacks aimed at these operations. However, the beginning of an alarming trend can be traced back to an attack that took place more than a decade ago. There were many historic critical infrastructure outages caused by natural catastrophe or system failure are at least somewhat useful in determining the consequences of cyberattacks on such infrastructure. Electricity is in itself very critical infrastructure, but all other critical infrastructure is also dependent on the power grid including water supply, energy supply, communication, transportation, healthcare, and banking. Finally, because cyberattacks are an entirely man-made threat, as opposed to the risks from natural hazards, motivation is an important factor in determining the probability of successful attacks.
Today's Headline in NewsHours
0:00 Intro
2:08 #CommerceIQ raises $60 million, looks to launch India operations by 2022
Technology video | 134 views

The National Critical Information Infrastructure Protection Centre in India, an organisation of the Government of India designated as the National Nodal Agency in respect of Critical Information Infrastructure Protection, has identified the following as ‘Critical Sectors’ – Power & Energy, Banking, Financial Services & Industrance, Telecom, Transport, Government and Strategic & Public Enterprises.
All of these, which provide services that are essential to the day-to-day functioning of society, are hives of the most sensitive and confidential data that threat actors can easily be monetised on the Dark Web, driving further cybercrime and disruption.
Unfortunately, the potential for widespread disruption has not gone unnoticed by cybercriminals. In India, close to seven critical infrastructure attacks have wreaked havoc for those within that industry – from the Oil India Limited ransomware attack in April, and in May on grounded SpiceJet flights, leaving passengers stranded for 4 hours, to Goa’s flood monitoring system in June and banking data breaches reported in August to the more recent cyberattacks on the AIIMS healthcare sector and resulting onslaught on Safdarjung Hospital in New Delhi, have left authorities understanding the need to prepare for an escalation in cyberattacks in future.
This focus on critical infrastructure is intentional. Cybercriminals are fully aware of the impact that any disruption has on vital services, not just financially but also on public confidence. For example, in utilities, you cannot expect people to be without electricity or water, which means companies are more likely to pay in the event of ransomware.
Hackers are also very observant and will strike during periods of unrest, for example using the ongoing energy crisis as an entry point for phishing or man-in-the-middle attacks.
Another common risk factor among critical infrastructure organizations is that they all have a hig
Technology video | 143 views

#Onlineracket #DelhiPolice #electriccar
Autonomous & electric car industry looming under cyber threat
Autonomous driving, connected cars, electric vehicles, and shared mobility – have dominated the agenda of automotive industry leaders in recent years. These innovations, built on the digitization of in-car systems, the extension of car IT systems into the back end, and the propagation of software, turn modern cars into information clearing houses. Hacking of connected cars by security researchers has made headlines over the past few years, and concerns about the cybersecurity of modern vehicles have become real. In order to excel at cybersecurity, new processes, skills, and working practices along the automotive value chain will be required. This includes identifying cyber risks, designing secure software and hardware architectures, and developing and testing secure code and chips, ensuring that issues can be fixed – even years later – via software updates. The rising need for cybersecurity will trigger investments over the next few years.
As our cars get more connected, the risk of cybersecurity breaches increases on board. While the industry charged with combatting vehicle hackers is booming, it’s a constant battle to keep up with increasingly sophisticated technology. A new standard has just been published to help manufacturers get one step ahead. ISO/SAE 21434 will help consider cybersecurity issues at every stage of the development process and in the field, increasing the vehicle’s own cybersecurity defences and mitigating the risk of potential vulnerabilities for every component. We expect to see the market grow to $9.7 billion in 2030, with software business representing half of the market by 2030. The strong growth of the market will create many new business opportunities for suppliers, established IT firms, specialist niche firms, start-ups, and many others, especially in the software development and ser
Technology video | 213 views

#Cryptocurrencies #Cybercrime #NSE
Cryptocurrencies & Cybercrime to go hand in hand
It is believed that #cryptocurrencies like #Bitcoin, #Ethereum, #Binance and USDT will change the future of global finance, which affects how we secure these securities in the future. But with a rise in cryptocurrency, comes the added risk of cybercrimes that only proper crypto cybersecurity can solve. There are now a vast number of different types of cryptocurrencies in use, and more are coming up every day. However, these digital assets are decentralized, unregulated, and independent, operating free of central banks. This makes an excellent opportunity for cybercriminals. Cybercriminals can hack into cryptocurrency trading platforms and steal funds. They can attack any business and ask for ransom in digital currencies as this form of cybercrime is untraceable, and no evidence leads back to the perpetrators. The technology that stands behind cryptocurrency allows both institutions and people to make transactions without the need for banks, governments, and other intermediaries. The decentralization of cryptocurrency is an excellent opportunity for cybercriminals. Cryptocurrency is already the most preferred form of exchange in cases of ransomware attacks.
With cryptocurrencies spreading across the business world, cybercrime has become a real threat. While cryptocurrency might be the dawn of a new age, cybercrime is also on the surge. It comes in many forms, from ransomware to email scams. It is estimated that 33% of bitcoin trading platforms have been hacked. The best way to protect businesses from these cyber-attacks is by implementing proper crypto cybersecurity protocols and adopting zero-trust security models to make these transactions more secure. This makes them affordable and free of fees. However, every professional and business should be worried about cybersecurity. However, where there is a chance to make money, there
Technology video | 215 views
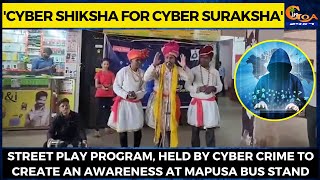
'Cyber Shiksha for Cyber Suraksha' Street play program, held by cyber crime to create an awareness at Mapusa bus stand
#Goa #GoaNews #streetplay #Cyber #crime #awareness #Mapusa
'Cyber Shiksha for Cyber Suraksha' Street play program, held by cyber crime to create an awareness
News video | 260 views

#SingleMaltWhisky #DadaBartender #CocktailsIndia
To fully appreciate the vast world of blended scotch whisky, it's helpful to understand the distinction between single malt and blended whiskey.
Consumers and even some bartenders have a misconception that single-malt Scotch is not a blended whisky, but this is a myth. Single-malt scotch is a blend, but it's a very specific type of blend. In fact, nearly all whiskies on the market today are blends—bourbons, ryes, Tennessee, scotches, etc.—although in this video I'll focus on Scotch.
The confusion arises from the misunderstanding of two words—blend and single—words whose seeming simplicity mask a more complicated reality.
so start learning by watching the video Cheers
This video is made with Zoom H1n Recorder
link to purchase: https://amzn.to/2HhCNXh
*************************************************
Affiliate Link
Where to Purchase BLUE TEA
Link: https://amzn.to/2R9erVh
Where to Purchase Egyptian Hibiscus Tea
Link: https://amzn.to/2TczDHh
Please follow me on Instagram: https://www.instagram.com/cocktailsin...
Please follow me on Facebook: https://www.facebook.com/cocktailsind...
Affiliate link
THIS VIDEO BEING SHOOT WITH CANON 700D CAMERA
LINK TO PURCHASE http://amzn.to/2CEZlPR
THE MIKE I HAVE USED IN THIS VIDEO IS RODE VIDEOMICRO
LINK TO PURCHASE http://amzn.to/2CrftkH
you can get this kind of blur image if you use canon 50 mm lens
this is the link http://amzn.to/2AM0iB4
Vlogs video | 4454 views

#Tighterregulations #ITminister #Ola
Critical Infrastructure - an undeclared battlefield
By 2025, 30% of critical infrastructure organizations will experience a security breach that will result in the halting of operations or mission-critical cyber-physical systems, as per the recent report from Gartner. Critical infrastructure security has become a primary concern for governments around the world, with the U.S., U.K. EU, Canada and Australia each identify sectors deemed ‘critical infrastructure’, for example, communications, transport, energy, water, healthcare and public facilities. In some countries, critical infrastructure is state-owned, while in others, like the U.S., private industry owns and operates a much larger portion of it. The recent massive cyber attack on Australian energy Infra by Chinese hackers, were just minutes away from shutting down power to three million Australian homes when they were foiled at the last obstacle. If the attack is successful, it will knock off electricity to between 1.4 and 3 million homes, with no way of knowing how long it will take to retake control of the generators. Experts say, what is the need to go for the complete automation of the Operational Technology. Operational technology, monitors and manages industrial process assets and manufacturing/industrial equipment. Essentially, OT is the hardware and software that keeps things, for instance factories, power plants, facility equipment etc. running.
“Governments in many countries are now realizing that their national critical infrastructure has been an undeclared battlefield for decades and they are now making moves to mandate more security controls for the systems that underpin these assets. A Gartner survey showed that 38% of respondents expected to increase spending on operational technology (OT) security between 5% and 10% in 2021, with another 8% of respondents predicting an increase of above 10%. Besides the need to
Technology video | 162 views

A New Report Details Wiper Malware Aimed at Ukraine and Upsurge in Cyber Threats from Likely Russian-backed Actor in the Fourth Quarter of 2021. It successfully targets high-ranking political leaders and executives. The fourth quarter of 2021 saw the world shift out of a two-year pandemic during which bad actors leveraged work from anywhere opportunities and Log4Shell was an unwanted holiday guest. During the first quarter of 2022, the focus on threats shifted to campaigns weaponizing cyberthreats against Ukrainian infrastructure in the Eurasia region conflict. The key findings from the report include individual consumers being the No. 1 target of cybercriminals, closely followed by the healthcare vertical. Additionally, the transportation, shipping, manufacturing and information technology industries showed a sharp increase in threats. There are critical junctures in cybersecurity and observing increasingly hostile behaviour across an ever-expanding attack surface, says an Expert. Our world has fundamentally changed. The fourth quarter signalled the shift out of a two-year pandemic which cybercriminals used for profit and saw the Log4Shell vulnerability impact hundreds of millions of devices, only to continue cyber momentum in the new year where we’ve seen an escalation of international cyber activity.
Trellix Threat Labs has been investigating wiper malware and other cyberthreats targeting Ukraine. Wipers render devices within targeted organizations useless by destroying the memory critical to how the devices operate. Trellix analysis of the Whispergate and Hermetic Wiper Malware used before and during the invasion of Ukraine details the similarities and differences of the two strains used to de-stabilize Ukrainian IT systems by destroying the communications within the country. Trellix observed the continued use of Living off the Land (LotL) methods, where criminals use existing software and controls native to a device to execute an attack. Windows Comma
Technology video | 121 views

This new world structure brings with it new security problems. Critical infrastructure organizations must use a robust framework that can anticipate and mitigate disaster across their entire #criticalinfrastructure environment.
India’s journey towards becoming a $5 trillion economy would remain incomplete without the use of digital technologies and they would need protection to build trust around them. Without adequate cyber security, the Indian economy would not be able to achieve its intended goals.
Rapid digitization and increased mobility offer many advantages while expanding the threat and vulnerability landscape. India has witnessed an increase in the number and frequency of recent data breaches, proving that companies across all sectors are vulnerable to #cyberattacks.
It is the need of the hour to make cyber security a national priority, since the rapid digitalisation of businesses, administrative functions of the government, etc., have resulted in frequent cyberattacks on India’s cyber assets. India needs to increase its investments on strengthening its cyber security framework.
It is also important to recognize the risks that could threaten the integrity of critical infrastructure systems. When we think about system or network security, we almost always immediately think of hacker or terrorist threats, but there are other threats that should also be taken into account, such as equipment failure, human error and natural causes (the weather, for example).
Developed economies are allocating separate funds for cyber security purposes and India should consider the same to ensure that 1% of its GDP is spent on cyber security to protect government systems, business ecosystems and the socioeconomic fabric of the country.
Critical Infrastructure Protection is to protect a region's vital infrastructures such as food and agriculture or transportation. Critical Infrastructure Protection helps organizations to
Technology video | 121 views

CERT-In warns organisations against Ransomware that targets critical infrastructure #shortsvideo
Technology video | 179 views

Bigg Boss 18 OPENING VOTING Trend | Vivian Vs Karan Vs Digvijay Kisko Hai Highest Votes
#biggboss18 #avinashmishra #viviandsena
Follow Aditi On Instagram - https://www.instagram.com/pihuaditi/
Bigg Boss 18 OPENING VOTING Trend | Vivian Vs Karan Vs Digvijay Kisko Hai Highest Votes
Entertainment video | 2091 views

Bigg Boss 18 Promo | Wild Card Entries Ne Avinash, Rajat Aur Vivian Ko Phasa Diya
#biggboss18 #avinashmishra #viviandsena
Follow Aditi On Instagram - https://www.instagram.com/pihuaditi/
Bigg Boss 18 Promo | Wild Card Entries Ne Avinash, Rajat Aur Vivian Ko Phasa Diya
Entertainment video | 1069 views

Yeh Rishta Kya Kehlata Hai | Abhir Ko Hoga Kiara Se Pyaar, Show Mein Love Angle
#yehrishtakyakehlatahai #yrkkh
- Stay Tuned For More Bollywood News
☞ Check All Bollywood Latest Update on our Channel
☞ Subscribe to our Channel https://goo.gl/UerBDn
☞ Like us on Facebook https://goo.gl/7Q896J
☞ Follow us on Twitter https://goo.gl/AjQfa4
☞ Circle us on G+ https://goo.gl/57XqjC
☞ Follow us on Instagram https://goo.gl/x48yEy
Yeh Rishta Kya Kehlata Hai | Abhir Ko Hoga Kiara Se Pyaar, Show Mein Love Angle
Entertainment video | 1092 views

Bigg Boss 18 | MID WEEK EVICTION | Shocking Ye Contestant Hoga Evict
#biggboss18 #avinashmishra #viviandsena
Follow Aditi On Instagram - https://www.instagram.com/pihuaditi/
Bigg Boss 18 | MID WEEK EVICTION | Shocking Ye Contestant Hoga Evict
Entertainment video | 960 views

Yeh Rishta Kya Kehlata Hai | Armaan Ke Karib Aayi Ruhi, Phir Pyaar Me Hui Beqaboo
#yehrishtakyakehlatahai #yrkkh
- Stay Tuned For More Bollywood News
☞ Check All Bollywood Latest Update on our Channel
☞ Subscribe to our Channel https://goo.gl/UerBDn
☞ Like us on Facebook https://goo.gl/7Q896J
☞ Follow us on Twitter https://goo.gl/AjQfa4
☞ Circle us on G+ https://goo.gl/57XqjC
☞ Follow us on Instagram https://goo.gl/x48yEy
Yeh Rishta Kya Kehlata Hai | Armaan Ke Karib Aayi Ruhi, Phir Pyaar Me Hui Beqaboo
Entertainment video | 956 views

Yeh Rishta Kya Kehlata Hai | Ruhi Par Bhadka Armaan, BSP Se Dur Rehne Kaha
#yehrishtakyakehlatahai #yrkkh
- Stay Tuned For More Bollywood News
☞ Check All Bollywood Latest Update on our Channel
☞ Subscribe to our Channel https://goo.gl/UerBDn
☞ Like us on Facebook https://goo.gl/7Q896J
☞ Follow us on Twitter https://goo.gl/AjQfa4
☞ Circle us on G+ https://goo.gl/57XqjC
☞ Follow us on Instagram https://goo.gl/x48yEy
Yeh Rishta Kya Kehlata Hai | Ruhi Par Bhadka Armaan, BSP Se Dur Rehne Kaha
Entertainment video | 961 views

মানুহৰ জীৱনৰ ধৰ্ম আৰু কৰ্ম কিহৰ দ্বাৰা পৰিচালিত হয়?
Vlogs video | 2288 views
ভগৱান শ্ৰীকৃষ্ণৰ জীৱন দৰ্শনৰ পৰা আমি কি কি কথা শিকা উচিত?
Vlogs video | 2333 views


চুতীয়া শব্দৰ উৎপত্তি আৰু চুতীয়া সকলৰ ইতিহাস
Vlogs video | 2075 views

Neel Akash live music show 2024 Rongali Bihu || Asin Ayang mane ki? ||
Vlogs video | 2322 views